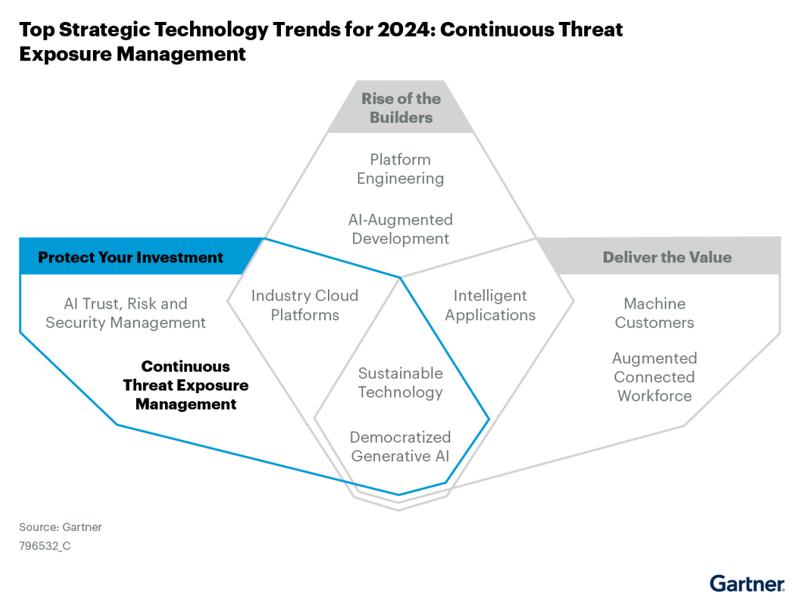
This article discusses the concept of Continuous Threat Exposure Management (CTEM) and its five stages, as well as key technologies that support its implementation. It also explores how CTEM differs from previous technologies in managing an organization’s attack surface.