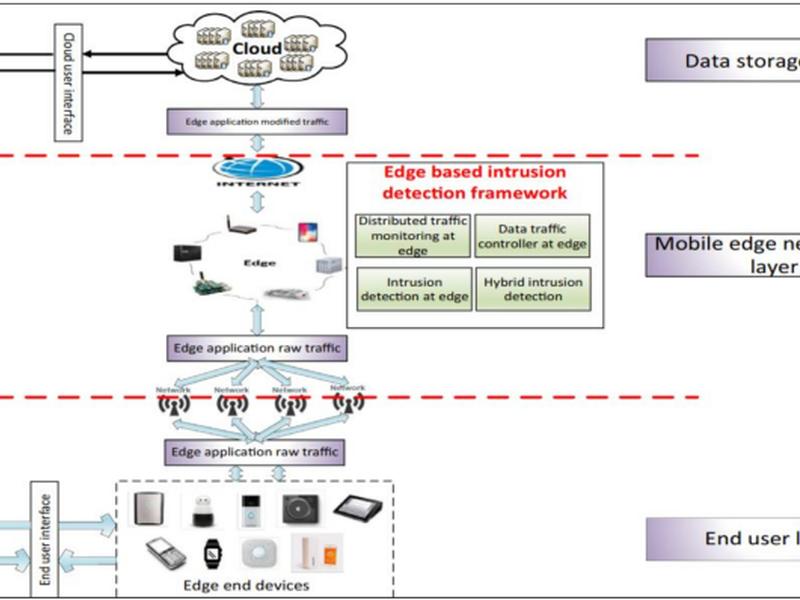
This article discusses various methods for protecting edge computing and IoT-based frameworks from intrusion detection and identification. The research analyzes existing studies and compares different techniques for multi-category detection. Some of the methods discussed include using support vector machines, deep neural networks, and convolutional neural networks. The article also highlights the challenges of identifying attacks like probing and privilege escalation in these systems.